Recommendation Info About How To Detect Network Intrusion
An ids can be designed to detect different.
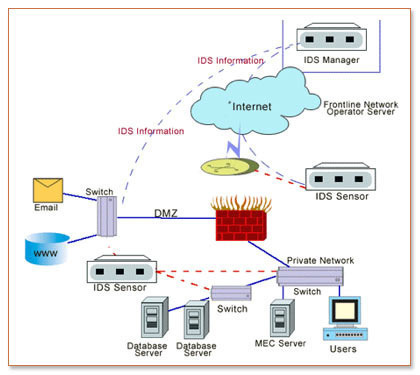
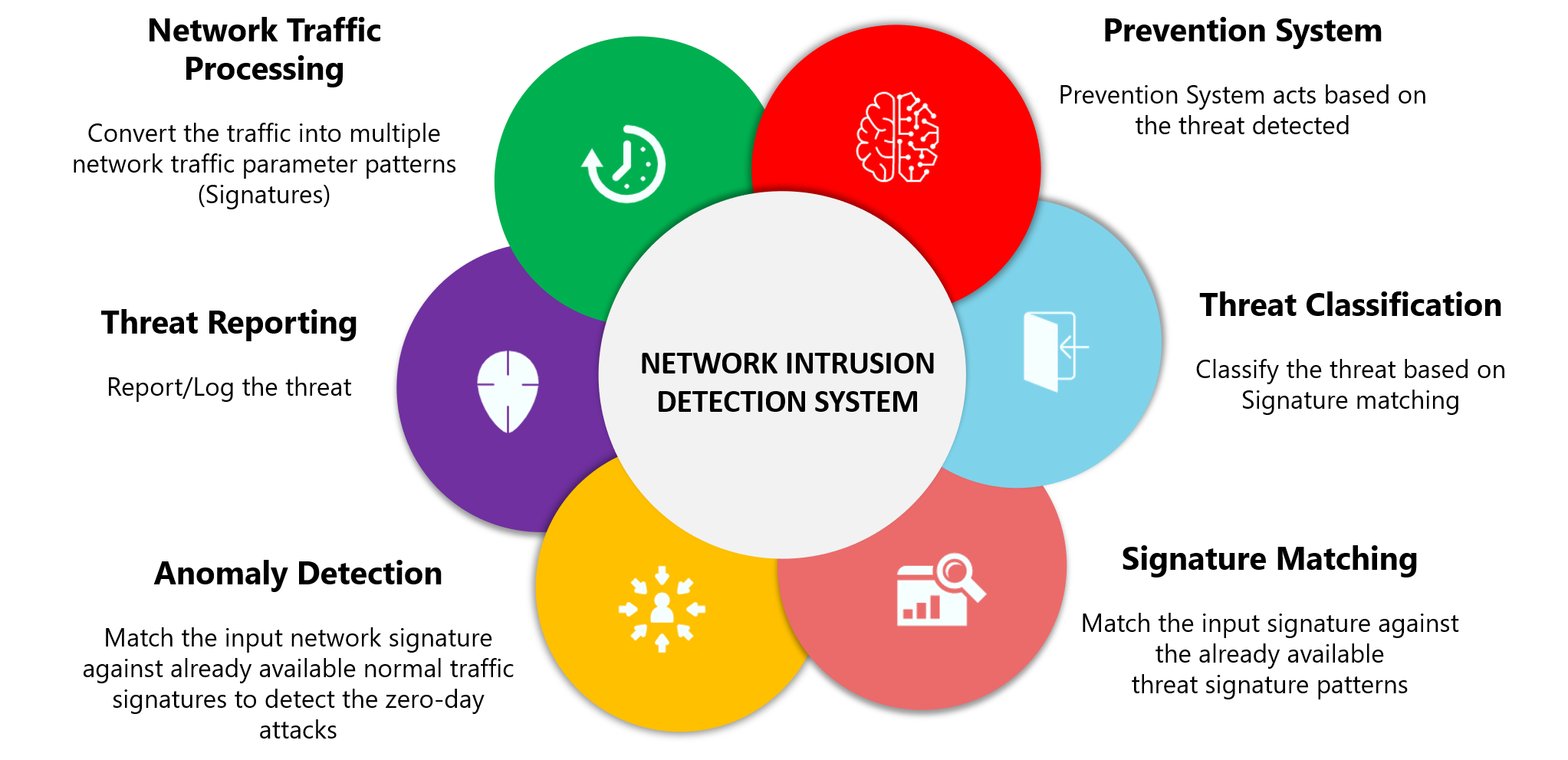
How to detect network intrusion. The ids informs the network security engineer through alerts that something may. The first thing you need to do is make sure your intrusion detection system did not trigger any false positive alarm. View network intrusion detection.docx from cse 145 at kl university.
Whenever a visitor opens the trusted website with his specific web browser, the web browser (of the visitor’s client remote machine) will automatically download the webpage. It's similar to how you would protect your physical office from an intruder. This hacking tutorial presents a crash course on the subject of packet analysis and intrusion detection.
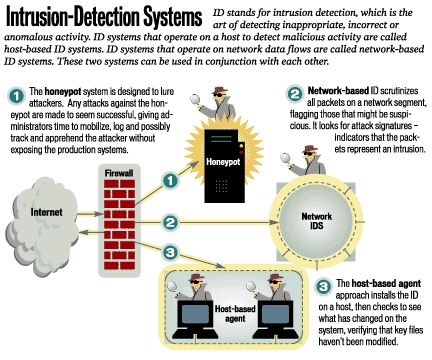
It carefully monitors the network traffic to detect threats that generate irregular traffic flows like ddos attacks, which is a particular type of. Thus, by monitoring the honeypot, an ids can detect when a network intrusion is being attempted. Detecting network intrusions can't be done with a single solution.
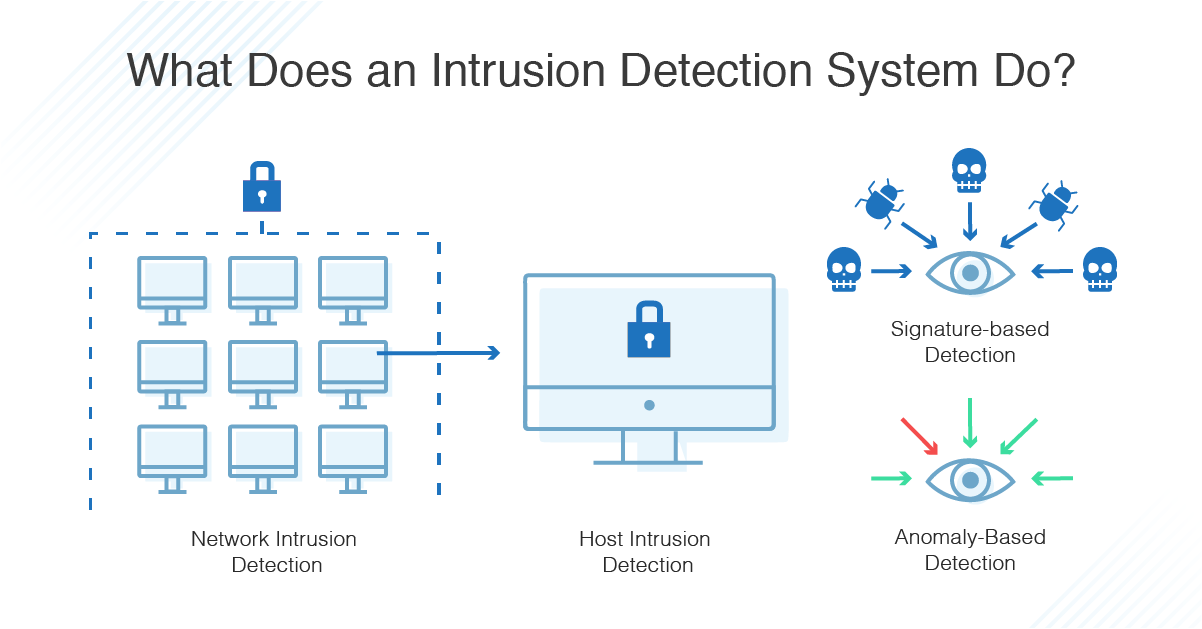
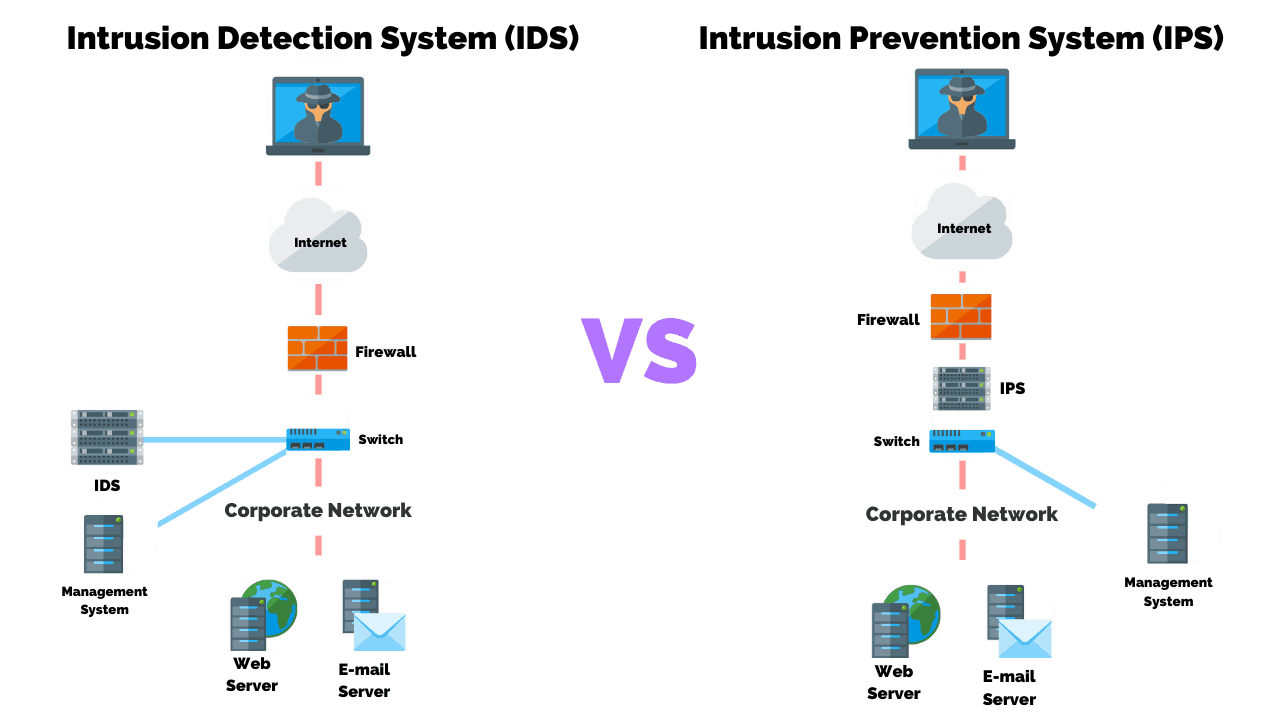
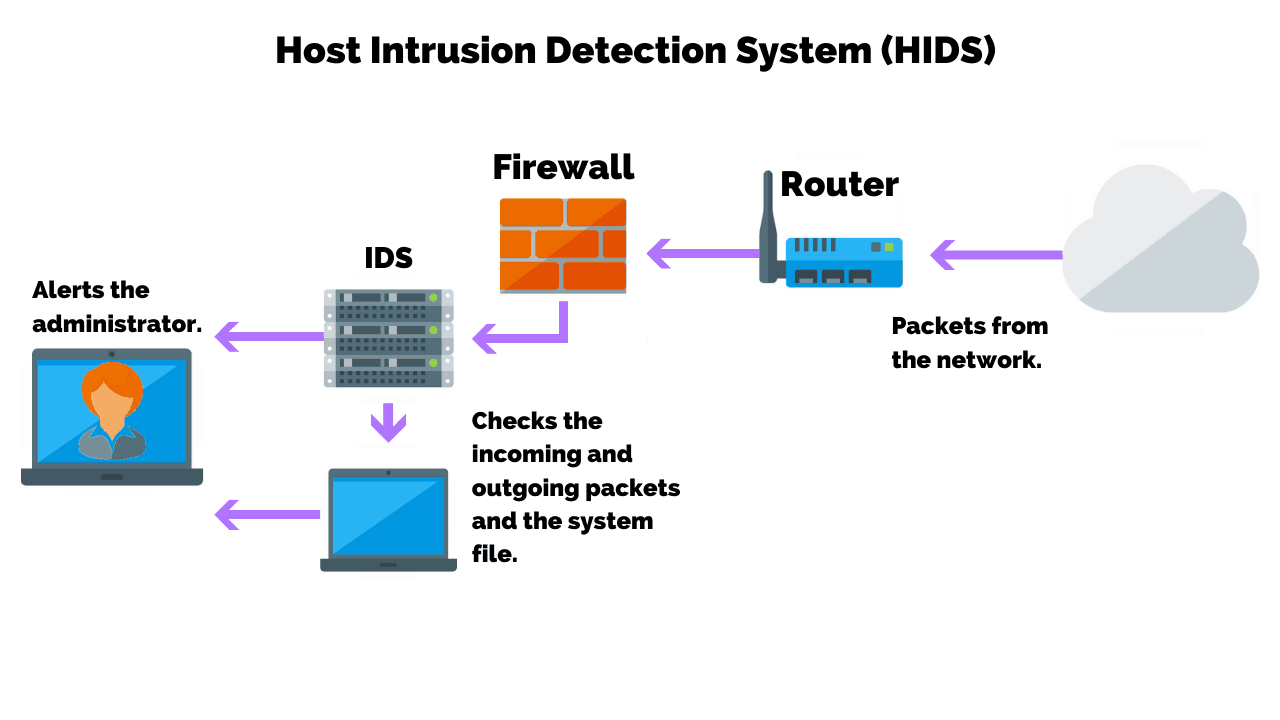
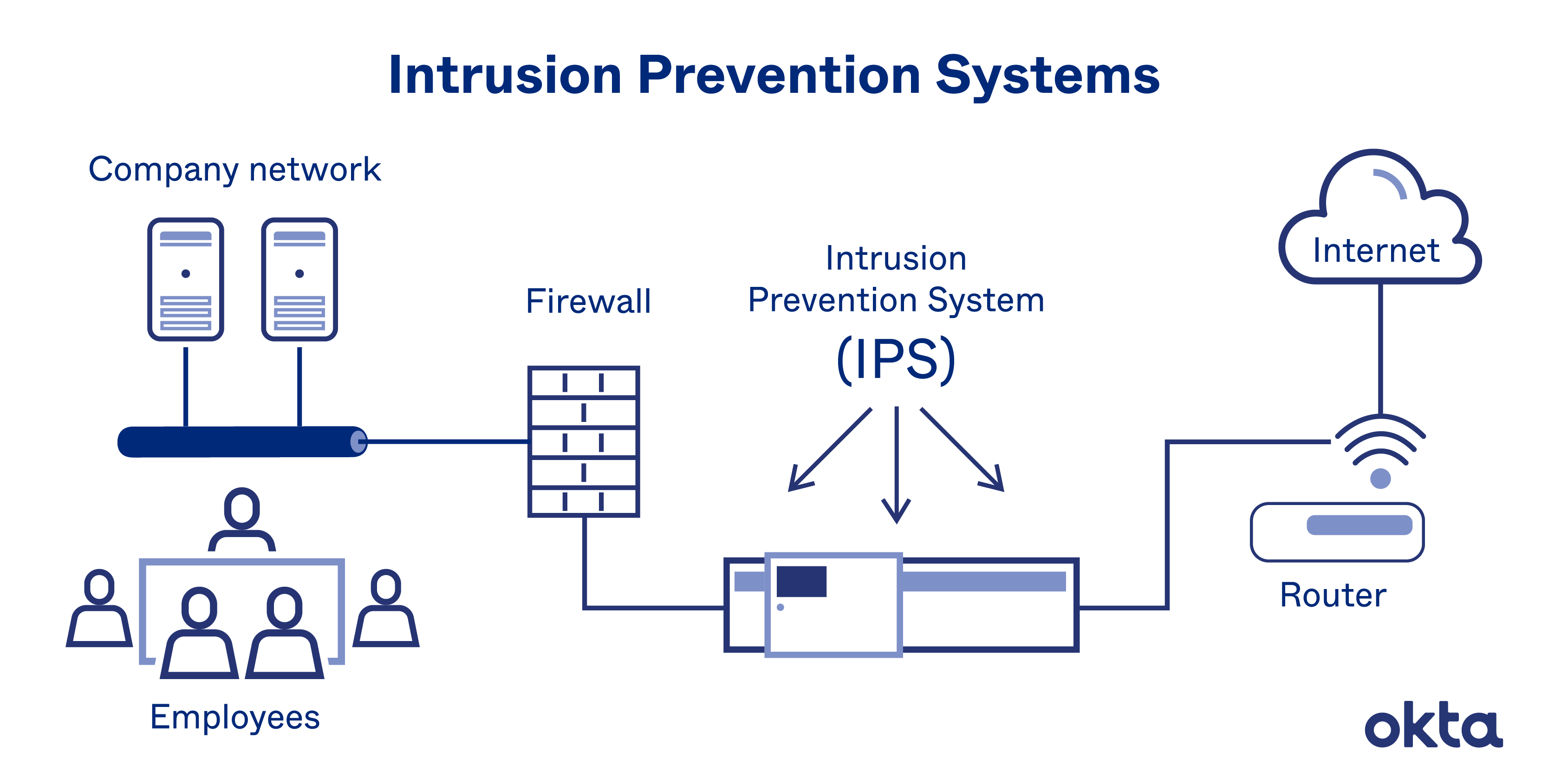
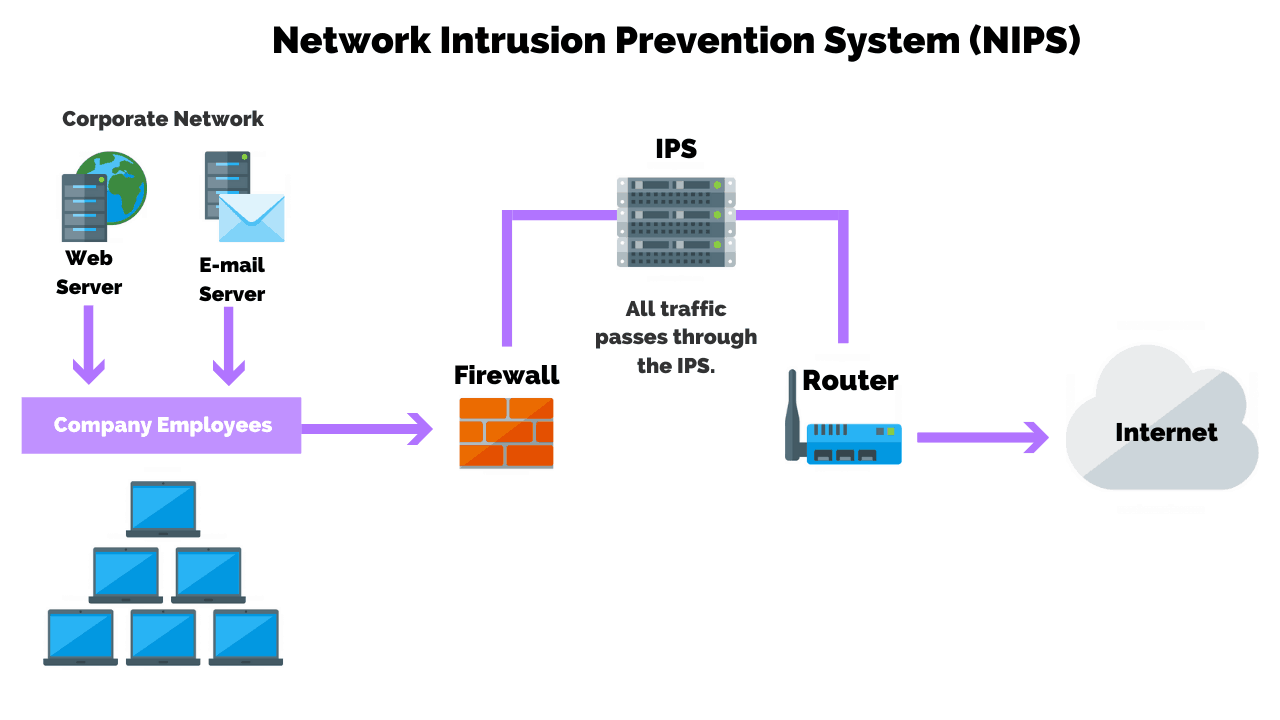
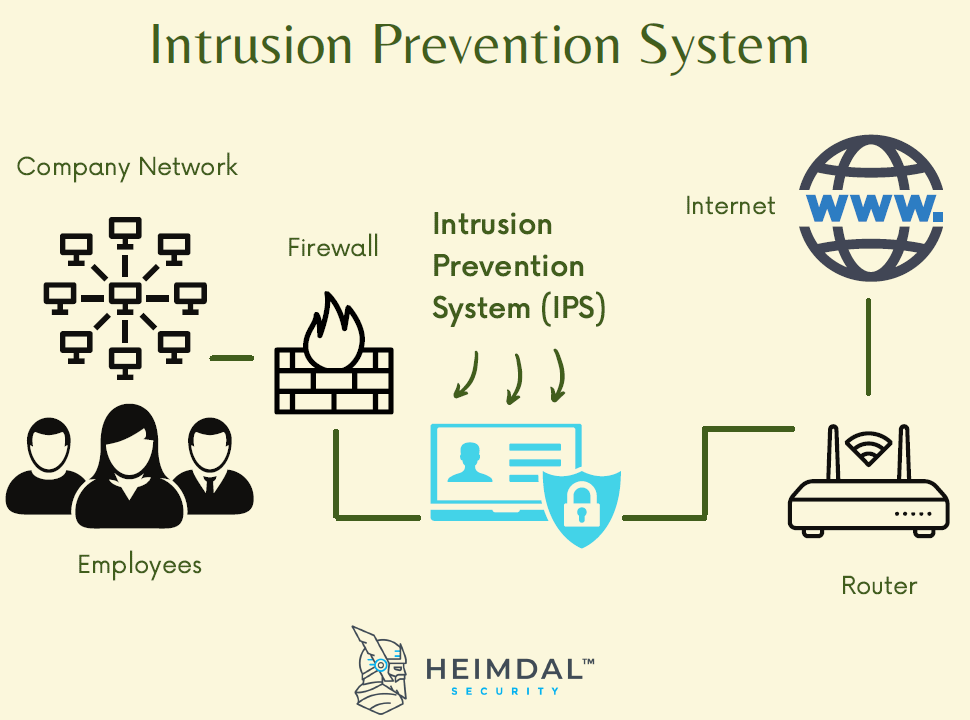
You can use analyzers to troubleshoot network problems and detect intrusions into your network. It’s advisable to integrate both host and network intrusion detection systems, as using only one can result in security vulnerabilities. An intrusion detection system ( ids) is a hardware device or software program that employs established intrusion signatures to recognize and analyze both incoming and outgoing network.
Detect network intrusions with wireshark and snort. By combining packet captures provided by network watcher and open source ids tools such as suricata, you can perform network intrusion detection for a wide range of. How to detect network intrusions knowing how to detect network intrusions is a key element of network security, and.
As you know that false positive alarms are those events that an. The psad intrusion detection system is available in ubuntu’s default repositories, so it can be easily acquired through apt: